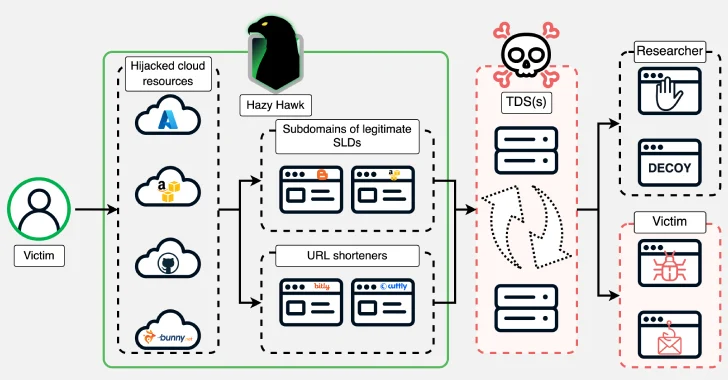
A threat actor known as Hazy Hawk has been observed hijacking abandoned cloud resources of high-profile organizations, including Amazon S3 buckets and Microsoft Azure endpoints, by leveraging misconfigurations in the Domain Name System (DNS) records.
The hijacked domains are then used to host URLs that direct users to scams and malware via traffic distribution systems (TDSes), according to Infoblox. Some of the other resources usurped by the threat actor include those hosted on Akamai, Bunny CDN, Cloudflare CDN, GitHub, and Netlify.
The DNS threat intelligence firm said it first discovered the threat actor after it gained control of several sub-domains associated with the U.S. Center for Disease Control (CDC) in February 2025.
It has since been determined that other government agencies across the globe, prominent universities, and international corporations such as Deloitte, PricewaterhouseCoopers, and Ernst & Young have been victimized by the same threat actor since at least December 2023.

“Perhaps the most remarkable thing about Hazy Hawk is that these hard-to-discover, vulnerable domains with ties to esteemed organizations are not being used for espionage or ‘highbrow’ cybercrime,” Infoblox’s Jacques Portal and Renée Burton said in a report shared with The Hacker News.
“Instead, they feed into the seedy underworld of adtech, whisking victims to a wide range of scams and fake applications, and using browser notifications to trigger processes that will have a lingering impact.”
What makes Hazy Hawk’s operations noteworthy is the hijacking of trusted and reputable domains belonging to legitimate organizations, thus boosting their credibility in search results when they are being used to serve malicious and spammy content. But even more concerningly, the approach enables the threat actors to bypass detection.
Underpinning the operation is the ability of the attackers to seize control of abandoned domains with dangling DNS CNAME records, a technique previously exposed by Guardio in early 2024 as being exploited by bad actors for spam proliferation and click monetization. All a threat actor needs to do is register the missing resource to hijack the domain.

Hazy Hawk goes a step further by finding abandoned cloud resources and then commandeering them for malicious purposes. In some cases, the threat actor employs URL redirection techniques to conceal which cloud resource was hijacked.
“We use the name Hazy Hawk for this actor because of how they find and hijack cloud resources that have dangling DNS CNAME records and then use them in malicious URL distribution,” Infoblox said. “It’s possible that the domain hijacking component is provided as a service and is used by a group of actors.”
The attack chains often involve cloning the content of legitimate sites for their initial site hosted on the hijacked domains, while luring victims into visiting them with pornographic or pirated content. The site visitors are then funneled via a TDS to determine where they land next.

“Hazy Hawk is one of the dozens of threat actors we track within the advertising affiliate world,” the company said. “Threat actors who belong to affiliate advertising programs drive users into tailored malicious content and are incentivized to include requests to allow push notifications from ‘websites’ along the redirection path.”
In doing so, the idea is to flood a victim’s device with push notifications and deliver an endless torrent of malicious content, with each notification leading to different scams, scareware, and fake surveys, and accompanied by requests to allow more push notifications.
To prevent and protect against Hazy Hawk activities, domain owners are recommended to remove a DNS CNAME record as soon as a resource is shut down. End users, on the other hand, are advised to deny notification requests from websites they don’t know.
“While operators like Hazy Hawk are responsible for the initial lure, the user who clicks is led into a labyrinth of sketchy and outright malicious adtech. The fact that Hazy Hawk puts considerable effort into locating vulnerable domains and then using them for scam operations shows that these advertising affiliate programs are successful enough to pay well,” Infoblox said.